A Beginner's Guide to THM Offensive Security Intro
Lab link :- Offensive Security Intro
Task 1 : What is Offensive Security?
"To outsmart a hacker, you need to think like one."
This principle captures the essence of Offensive Security—a proactive approach to cybersecurity. It involves simulating real-world attacks by breaking into systems, exploiting vulnerabilities, and identifying security gaps, all to strengthen defenses against malicious hackers. By understanding how hackers operate, organizations can stay one step ahead in securing their systems.
Starting Your Ethical Hacking Journey
In this TryHackMe room, you'll take your first steps into ethical hacking by safely practicing on a simulated environment. You'll learn how to think like an attacker while working within legal boundaries, gaining hands-on experience in identifying and exploiting vulnerabilities.
Next Steps
Answer the review questions to solidify your understanding of the core concepts. When you're ready, proceed to Task 2 and start exploring the world of ethical hacking!
Which of the following options better represents the process where you simulate a hacker’s actions to find vulnerabilities in a system?
- Offensive Security
- Defensive Security
Task 2: Hacking Your First Machine
At TryHackMe, Virtual Machines (VMs) are used to create realistic, controlled environments that allow for hands-on learning in a safe manner. These environments replicate real-world systems, enabling you to practice hacking techniques without any risk.
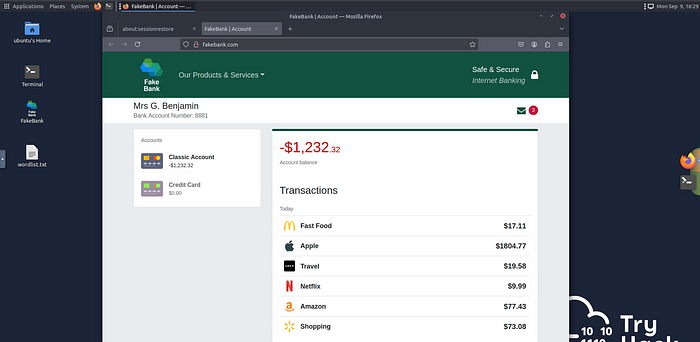
Introducing Fakebank
In this room, you'll interact with Fakebank, a simulated banking application designed specifically for hacking practice. You can explore its vulnerabilities and learn how ethical hackers identify and exploit weaknesses in web applications.
Starting the Machine
- Click the Start Machine button below to launch the VM.
- Your screen will split into two parts:
- Left side: This content and instructions.
- Right side: The browser interface for the Fakebank application.
If you accidentally hide the split view, you can restore it by clicking the Show Split View button at the top of the page.
Once the machine is fully set up, you’ll see a browser window displaying the Fakebank website. Use this opportunity to dive into the simulated environment and start exploring the vulnerabilities it offers!
Access the Machine:
- Launch the machine provided in the room and connect to it via the terminal.
List Files and Directories:
- Use
pwdto check the current directory. - Use
ls -hlagto view files within the directory. - Directory Bruteforce:
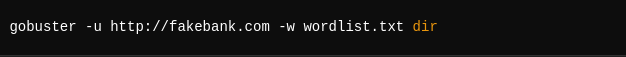
- You’ll use a tool like gobuster to brute-force the website directories.
- Run the following command to search for hidden directories:
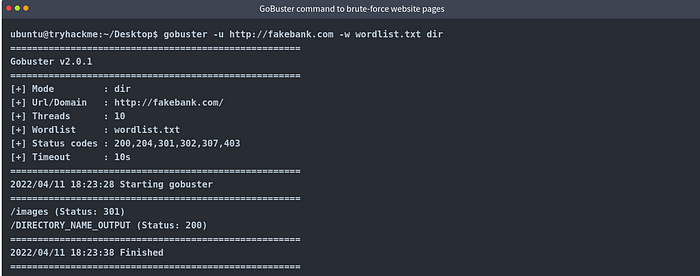
This will discover a directory called /bank-transfer.
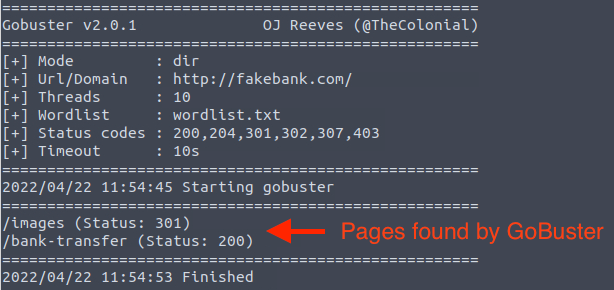
The /images endpoint responds with a status code of 301, indicating a redirection, while /bank-transfer
returns a status code of 200, meaning the page is accessible and
functioning properly at that location. The 200 code signifies a
successful request.
Access the Bank Transfer Page:
- Go to the URL
http://fakebank.com/bank-transferand perform a bank transfer by filling in the required fields. Once successful, check the balance on your account page for the flag.
Task 3: Careers in cyber security
Summary :)
To start learning cybersecurity, it’s important to break the field into smaller, manageable areas of interest. Focus on one specific area, practice regularly with hands-on exercises, and make learning a daily habit. Platforms like TryHackMe offer a structured path to gaining practical knowledge, and with consistent effort, you can secure your first job in the industry. Several success stories highlight individuals who transitioned from various fields into cybersecurity, showing that it’s achievable with dedication.
Offensive security careers include roles like:
- Penetration Tester: Finds security vulnerabilities in systems.
- Red Teamer: Simulates adversary attacks on organizations.
- Security Engineer: Designs and monitors security controls to prevent attacks.
With continuous learning and practice, you can make the leap into these roles!
Thank you so much for reading my blog! Your time and support mean everything to me. If you found the content helpful or insightful, feel free to like, comment, and share it with others who might benefit from it. I appreciate every bit of feedback and engagement — let’s keep the conversation going and continue learning together!

Join the conversation